Cryptography plays a crucial role in securing data and for enabling digital rights management. Cryptographic keys facilitate the encryption and decryption of data, ensuring the privacy and integrity of information exchanged.
While cryptography plays a crucial role in protecting access to data, the management of keys is also cited as one of the challenges to the widespread adoption of decentralised technology at population scale. This is because implementation requires people to manage passphrases, much like they manage passwords and PINs today, with the added complexity that resetting a passphrase is not as simple as resetting an email password or a PIN for a payment card.
With practical implementation front of mind, we work with our customers to set up the most appropriate approach to key management that balances both security and convenience for everyone in the network. When working with regulated bodies such as financial institutions, governments, and telecommunications providers it is generally regarded that the institutions have the necessary governance in place to help customers in the case of loss, theft or account lock-out. This is normally preceded by a Know Your Customer (KYC) onboarding such that bidirectional trust can be established. It is in this context that we generally find these institutions prefer to utilise a combination of decentralised and cloud services, so that service orchestration and support can be provided.
Within Meeco's Secure Value Exchange (SVX) we use a specific hierarchy of cryptographic keys, each with a distinct purpose and responsibility. The keys' functionality is designed in line with the guidelines from the National Institute of Standards and Technology (NIST) (800-57 Part 1), thus providing a reliable and secure architecture. Types of cryptographic keys include:
Here is how it works:
Securing the data:
The process begins with a Data Encryption Key (DEK) and a Keypair. These keys are necessary for encrypting and securing the data.
Protecting the keys:
A Key Encryption Key (KEK) is generated. The KEK is a new symmetric key, and its purpose is to encrypt the DEK and the private key of the Keypair.
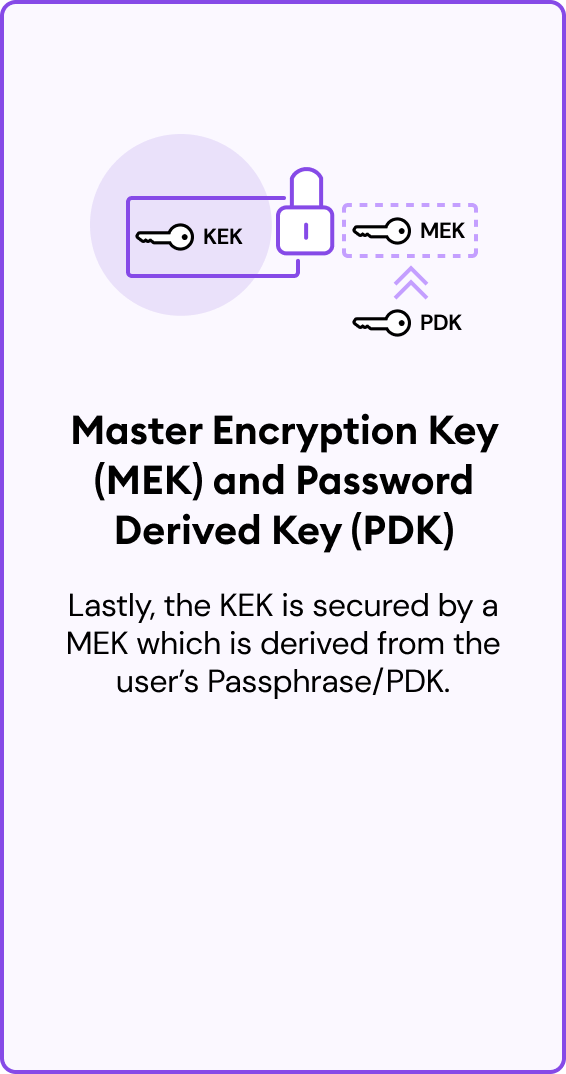
Protecting the encryption keys:
To ensure the security of the KEK, it is further encrypted by a symmetric key known as the Master Encryption Key (MEK). The MEK is derived from the end user's input via a process called a Password-Based Key Derivation Function (PBKDF2). This end user input is known as the Passphrase/Password Derived Key (PDK).
In essence, this hierarchy provides a structured and secure method for managing keys and accessing encrypted data, with each key playing a critical role in the overall process.
All personal data at rest is encrypted with symmetric key encryption based upon AES-256-GCM. Additionally, all data is encrypted on a per user basis. If data is exchanged vault to vault a unique and encrypted shared space is generated. For each encryption space, each user has different symmetric keys.
In addition to the encryption, the SVX Vault and Key Store can be further secured through a unique personal log-in and/or device PIN Code.
For full transparency, Meeco makes this important documentation publicly available and has published additional information about the key encryption library, which is open sourced and available on GitHub for review and auditing.
Read more